Sign in with Setapp
Overview
"Sign in with Setapp" is a public authentication mechanism that allows Setapp users to access apps using their Setapp account. Developers, in their turn, can use "Sign in with Setapp" to authorize their apps to communicate with our servers on behalf of the registered Setapp users.
"Sign in with Setapp" is perfect if your app has versions for platforms other than macOS or iOS or if you prefer not to use the built-in auth mechanisms of Setapp macOS Library and Setapp Framework.
The sign-in process follows the OAuth 2.0 Authorization Code Grant protocol. After a successful sign-in, your app receives an access token that allows further work with the Setapp Resource API.
The authentication stages are the following:
-
Using the Authorization Request URL, your app redirects a user to the Setapp sign-in page.
-
The user signs in using the Setapp credentials. The valid credentials allow the Setapp system to recognize a user with an existing (not deleted) account. However, at this stage, we're not checking the subscription status; you'll need to do it later using the
POST /accessrequest of the Vendor API. -
Once authenticated, the user authorizes your app to access the personal data using the dedicated Setapp dialog.
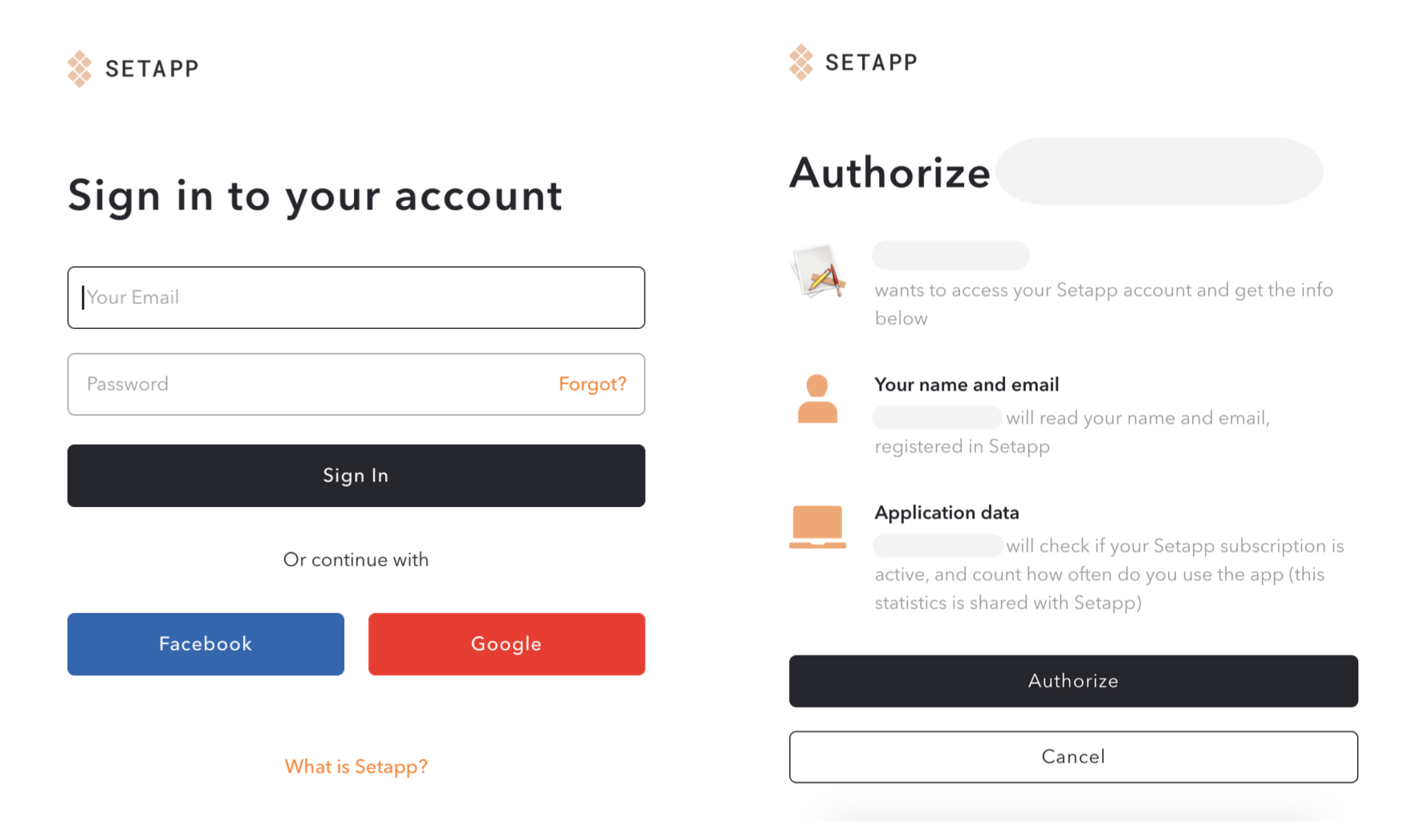
- The user is then redirected to the URI you specify for the authentication mechanism. The Setapp server passes the auth code within the redirect URI.
Redirection URIs
The essential elements of "Sign in with Setapp" are:
1. Authorization Request URL: the personalized "Sign in with Setapp" link will be embedded into your app. The URL is generated by the Setapp system based on the client ID of your app.
2. Redirection URIs to which users are redirected after passing or failing the sign-in.
You can submit all the Redirection URIs and view the Authorization URL in your developer account. See
the OAuth Clients article.
Updated 12 months ago
